Videos worth watching
More videos

AI is Killing Bug Bounties – Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️ @endingwithali → Twitch: https://twitch.tv/endingwithali Twitter: https://twitter.com/endingwithali YouTube: https://youtube.com/@endingwithali Everywhere else:

Clawdbot Malware
https://jh.live/hex-rays || Disassemble, decompile and debug with IDA Pro! Use promo code HAMMOND50 for 50% off any IDA Pro product

I Was Trapped in Chinese Mafia Crypto Slavery | Hacklab | WIRED
It began with a message in WIRED technology journalist Andy Greenberg’s inbox, sent from a lawless stretch of Laos bordering

AI wrote a hit piece
https://jh.live/continuumcon || Register for ContinuumCon 2026! The cybersecurity conference that never ends. 😎 Learn Cybersecurity and more with Just Hacking

Paralympian Answers Paralympics Questions | Tech Support | WIRED
United States Paralympian “Monster” Mike Schultz joins WIRED to answer the internet’s burning questions about Paralympic snowboarding, prosthetics, and more.

this is really funny
https://jh.live/flare-021426 || Manage threat intelligence and your exposed attack surface with Flare! Try a free trial and see what info
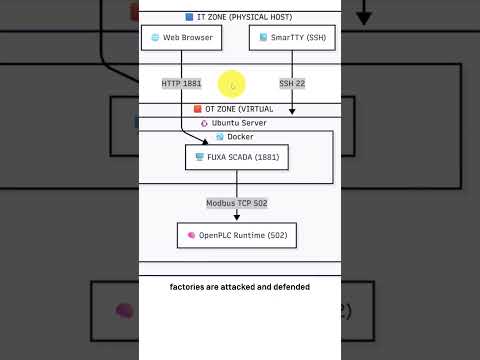
Build a Real ICS Cybersecurity Lab
Stop learning ICS security from theory alone. This short previews a hands-on tutorial where you build a realistic, attackable ICS

CISA Director Uploaded Documents to ChatGPT – Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️ @endingwithali → Twitch: https://twitch.tv/endingwithali Twitter: https://twitter.com/endingwithali YouTube: https://youtube.com/@endingwithali Everywhere else:

Build an ICS Cybersecurity Lab: OpenPLC, FUXA & Docker (Step-by-Step)
Most people try to learn Industrial Cybersecurity and OT security by reading PDFs and theory. That doesn’t work. In this
Latest

Future MacBooks May Hide Your Screen From Strangers
Apple is set to bring built-in privacy screen technology to future MacBooks within the next three years, according to a






![🔴 [PAYLOAD REVIEW] WiFi Pineapple Pager 📟🍍](https://i4.ytimg.com/vi/O_B989vdYHM/hqdefault.jpg)