Linux treats anything pulled from outside the system as untrusted until it is checked, and that expectation shapes how files
Life with the Penguin
Recent news

Open design: the opportunity design students didn’t know they were missing
What if you could work on real-world projects, shape cutting-edge technology, collaborate with developers across the world, make a meaningful

Anbox Cloud 1.28.0 is now available!
Enhanced Android device simulation, smarter diagnostics, and OIDC-enforced authentication The Anbox Cloud team has been working around the clock to

Ubuntu 18.04 EOL: Understanding Security Management and Risks
Linux security depends heavily on whether a system is still inside its support window. When that window closes, the system
Latest

Carol seeks the truth (serum) in Pluribus episode 4
Last week one of my big questions about Pluribus was whether our reluctant hero Carol (Rhea Seehorn) would find someone

Canonical Kubernetes officially included in Sylva 1.5
Sylva 1.5 becomes the first release to include Kubernetes 1.32, bringing the latest open source cloud-native capabilities to the European

Boosting Linux Security with DevOps Platforms for Automation and Compliance
Most production workloads still land on Linux. That hasn’t changed. What’s shifted is how teams manage those systems at scale”especially

Everything you need to know about FIPS 140-3 on Ubuntu | Videos
We get a lot of questions about FIPS 140-3, and so we decided to put together this comprehensive collection of

83% of organizations see value in adopting open source, but report major gaps in security and governance
A new Linux Foundation report reveals how organizations worldwide are adopting, using, and perceiving open source software. The Linux Foundation’s

Linux Fundamentals Are Drifting, and Your Security Can Fall Apart
You start to notice a pattern once you’ve spent enough time in incidents. Linux holds steady until the parts meant

A CISO’s preview of open source and cybersecurity trends in 2026 and beyond
Where is open source going next? What’s in store for open source in the coming years, particularly in relation to

Keylogging in Linux (Part 3): Kernel Techniques for the Keyboard Driver Path
Part 1 covered how Linux keylogging works in user space and why attackers lean on simple hooks or device access

Linux Security: Mitigating Model Inversion Attack Risks
Machine learning now runs deep inside Linux security workflows, from containerized inference services to open-source model pipelines. These systems look

Keylogging in Linux (Part 2): Advanced Techniques in the Linux GUI and X Server
Why Advanced Keylogging Techniques Depend on the Linux GUIAdvanced keylogging leans on the Linux GUI because once a user signs
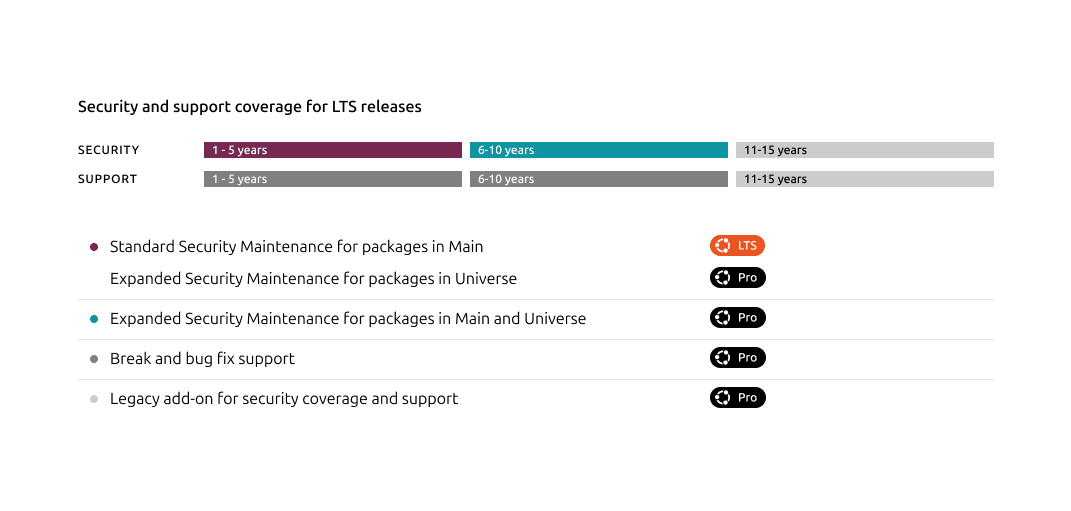
Canonical expands total coverage for Ubuntu LTS releases to 15 years with Legacy add-on
Ubuntu Pro now supports LTS releases for up to 15 years through the Legacy add-on. More security, more stability, and

Keylogging in Linux (Part 1): Understanding Attacks and Defenses
Keylogging turns up more often than people think. You see it in audits, red team work, and during investigations where

Canonical releases FIPS-enabled Kubernetes
Today at KubeCon North America, Canonical, the publisher of Ubuntu, released support to enable FIPS mode in its Kubernetes distribution,

Generating accessible color palettes for design systems … inspired by APCA!
This is the first of two blog posts about how we created the color palette for a new design system

Kernel Panic in Linux: Causes, Diagnosis & Fixes (2025 Guide)
A kernel panic still means the same thing it always has ” the Linux kernel hit a fault it couldn’t

Canonical announces optimized Ubuntu images for Google Cloud’s Axion N4A Virtual Machines
This new release brings the stability and security of Ubuntu to Axion-based N4A virtual machines on Google Compute Engine. November

Linux Desktop Adoption Surges to 5% with Security Gaps Identified
Linux just cleared 5% of the U.S. desktop market, based on recent Linux adoption statistics. That’s small in absolute terms

SonicWall: Firewall Management and Security Lessons After Breach
SonicWall confirmed a breach in its cloud backup system that exposed customer configuration files. It’s the kind of incident that

GNOME 50: Wayland-Only Brings Enhanced Security and Isolation
GNOME 50 finally drops X11 for good. Jordan Petridis called it on the GNOME blog, and the change landed with

Web Engineering: Celebrating Our Third Annual Hack Week
The Web Engineering team is thrilled to announce the successful conclusion of our third annual Hack Week! Over the past

Linux Kernel Security 2025: Curly COMrades Exploits and Risks Exposure
Linux security entered new territory in 2025. Espionage groups that once focused on Windows began treating Linux as equal ground.



